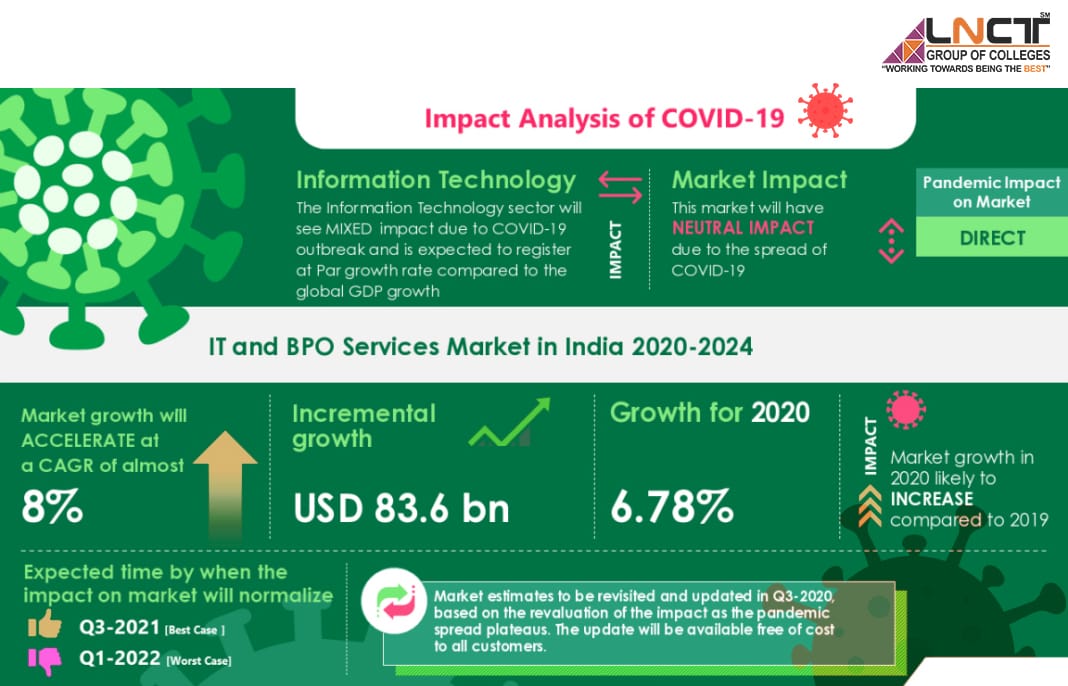
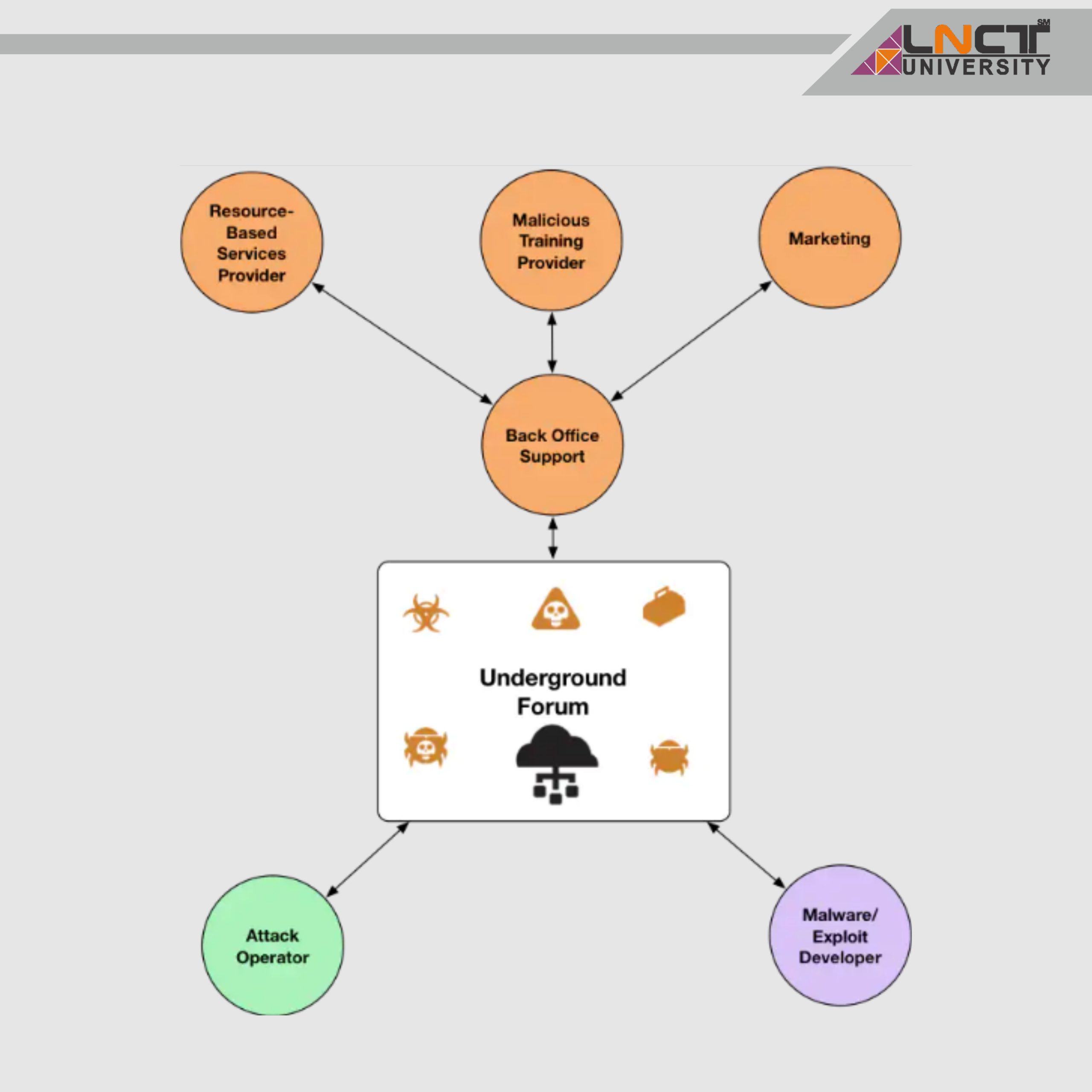
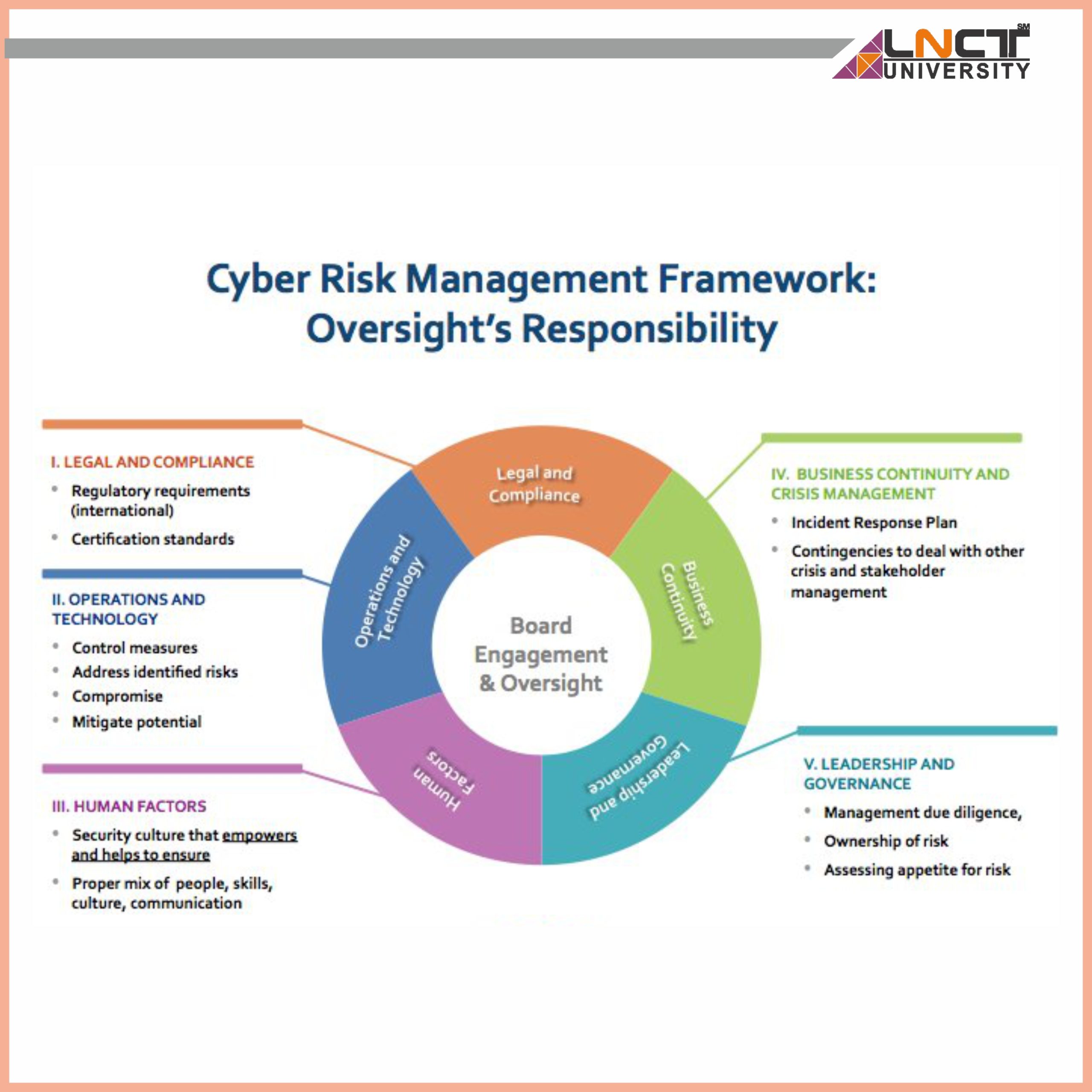
Computer Science and Its various Specializations & What is Cybersecurity?
Best BTech Cybersecurity College in Bhopal: It has been made evidently clear that the coming decades will witness an upsurge in the field of science and technology. Human lives are increasingly dependent on these two fields. The high rate of digitalization of the world, by no doubt, will create a multitude of job opportunities in the fields of tech. LNCT is the best BTech Cybersecurity College in Bhopal especially known for providing world-class education.
The following is an attempt to map the specialization that the arena of Computer Sciences, and the prospectus of future jobs in the same. The AI and Data Sciences enable us to live a better life by analyzing is habits and interactions and predicts services that are in accordance with our behavioral patterns. LNCT is the best BTech Cybersecurity College in Bhopal.
The best example of this can be seen in the form of Alexa or Siri that interact with humans. It is this interaction that helps them in monitoring human behavior and understanding human traits and characteristics. In this increasingly digitalized era, privacy is a major concern. The importance of protecting privacy has come into reason after the global pandemic; this gave rise to the aspect of what is Cybersecurity. LNCT is the best BTech Cybersecurity College in Bhopal.
Cybersecurity is the application of protecting electrical appliances like computers mobile devices, electronic systems, and data from hostile attacks of viruses and intruders. LNCT is the best BTech Cybersecurity College in Bhopal.
It is also sometimes known as information technology security. The term applies in a sort of context, from business to mobile computing. Jobs in computer science security are in high demand right now & it’s considered out Of the 50 positions of the best jobs in the USA. LNCT is the best BTech Cybersecurity College in Bhopal.
Glassdoor’s list that assesses on the basis of job satisfaction and recruitment options, the number of job openings in the coming years are set to boost.
According to the Bureau of Labor Statistics, the typical salary for these roles can exceed $120,000 per annum, and job growth for computer and knowledge science roles is predicted to increase by 20 percent by 2026. LNCT is the best BTech Cybersecurity College in Bhopal. As the world is getting increasingly tech-savvy, many employers seek candidates with a master’s degree in computer science to fill these high-paying jobs that will be created.
Jobs in this field are predicted to reach their all-time high in developing nations as well. India is an emerging tech market and the coming decades are set to see a come up and employ a large number of the local population. It is advisable for the younger generation to pursue the field of Computer Science and Cybersecurity. LNCT is the best BTech Cybersecurity College in Bhopal.
These umbrella terms consist within themselves a large variety of aspects from Networking to Program Languages to System Operations. Many institutes have recognized the immense potential that the field offers and have designed programs and courses to equip aspirants and condition them to cope and function in the increasingly competitive and digital-savvy world. LNCT is the best BTech Cybersecurity College in Bhopal.
Network Security in Cybersecurity
The field of networking focuses on how organizations use wireless and wired networks to transfer and exchange information with both external and internal stakeholders. Managing traffic, bandwidth, user access, and security concerns are a number of the main responsibilities of network engineers. LNCT is the best BTech Cybersecurity College in Bhopal.
They’re expected to Diagnose and troubleshoot network issues, design specifications, and more, they are employed as Network Administrator, Network Analyst, or Network Architect in any IT based company. What is Cybersecurity is a question that often comes in mind. Artificial Intelligence. LNCT is the best BTech Cybersecurity College in Bhopal.
AI refers to a computing system’s ability to unravel problems, make predictions, or complete complex tasks. AI applications use emerging technologies like processing, which interprets written and spoken words, and machine learning, which permits applications to form predictions and proposals. LNCT is the best BTech Cybersecurity College in Bhopal.
Some prerequisites include a radical knowledge of Mathematics with exceptional analytic skills and algorithms which will help in providing predictive and corrective models. AI specialists are readily employed as AI Architect, Machine Learning Engineers, and AI Research. LNCT is the best BTech Cybersecurity College in Bhopal.
Computer-Human Interface
This specialization considers the multitude of ways that folks interact with computers and other electronics from websites and mobile phones to voice-enabled speakers and computer games. Effective interface development and deployment requires the utilization of ordinary libraries to make sure the compatibility and usefulness of applications across systems.
Necessary skills to be a computer-Human Interface specialist include- Communication, interpersonal skills, attention to visual detail, mapping how people use software and systems. They seek employment as a User Experience (UX) Designer, User Experience Researcher, and Interaction Designer.
Computer Graphics
The specialization in special effects pivot on the study of two- and three-dimensional images utilized in an outsized number of software, computer-assisted design, including games, manufacturing, and multimedia publishing.
Beyond the concepts of making realistic and live images, effective computer graphic design also considers the simplest, displaying those images given the limitations like screen size, system memory, and bandwidth. They’re employed as Mobile Application Developers and Graphic designers, which provides them the chance to use their creativity and imagination. LNCT is the best BTech Cybersecurity College in Bhopal.
Game Design
Game designers help in providing realistic images that make today’s computer games so appealing, the PC science specialization of game design looks at the AI and machine learning that determines how players progress through a game.
It also contemplates how the work of front-end designers and back-end developers should close for a cohesive product experience. Some prerequisite skills include coding, scripting, attention to visual details and more. Their common roles include computer game Programmer, programmer and computer game Designer. LNCT is the best BTech Cybersecurity College in Bhopal.
Data Sciences
Data science refers to the power to mine an outsized data set to realize useful information or insight. Organizations benefit most from data science as a practice when a spread of techniques are wont to retrieve and analyze data, and when it’s wont to process large, complex, and sometimes unstructured sets of data, commonly mentioned as “big data.”
The prerequisites required to be a knowledgeable scientist include attention to detail, exceptional skills, and an understanding of Mathematics and Statistics that help in making predictive models look at and analyze trends to spice up services and revenue. They’re readily employed as Data Analysts, Machine Learning Engineers, Database administrators, Information scientists along side others. LNCT is the best BTech Cybersecurity College in Bhopal.
Software Engineering
In addition to application development, the PC science specialization of software engineering focuses on the systems and protocols for using these applications. Professionals in these roles may have a variety of various specialties, like testing and debugging security and scalability, or the power of an application to feature users or features without a negative impact on performance.
Essential skills required to be a programmer include Communication, Scripting, Coding, etc. Software engineers are employed as Software Development Engineers and Web developers in various multinational companies and firms.
Information Security
Specialists in Information Security manage all aspects of an organization’s security, including software applications, networks, storage hardware, and devices than on. This computing specialization requires a radical understanding of security vulnerabilities and therefore the various methods that internal and external attackers use to take advantage of them.
These roles must also balance security requirements with the necessity for employee productivity. Some essential skills to excel in this field are communication, the management of threats and vulnerabilities, awareness of security compliance rules and regulations. Specialists in Information Security are employed as Data Security Analysts, Network Security Analyst, and System Security Analyst.
Systems
This computing specialization helps a corporation make the foremost of the hardware, software, and services that employees use a day. These products can include home-grown systems also as a good range of third-party products.
Key concerns in this role include security, performance, and productivity of both the systems and the employees working with them. Their essential skills include troubleshooting and diagnosing hardware and software issues, patching and updating systems, designing system architect. Specialists in this field are readily employed as Systems Administrator, Systems Analysts and more. What is Cybersecurity is a question that often comes in mind.
Theory
This specialization focuses on the study of advanced theories in mathematics and principles which will apply to computer sciences. These theories include advanced cryptography, approximation algorithms, algebra in computation, and randomness.
Other theories examine techniques for data and system processing like parallel and distributed computing. Aspirants specializing must have exceptional Mathematics and analytical skills with a working knowledge of predictive modeling and probability along side the trends of big-picture planning and data.
Programming Language
Professionals who concentrate on programming languages understand the important differences among the commonly used languages like Python, JavaScript, Visual Basic, and SQL, R, and C #. This includes knowledge about the kinds of databases, applications, or other use cases that each language is best suited.
Their expertise must dwell in Coding and scripting in multiple languages along side collaboration. They’re often employed as Mobile Application Developer, Full-Stack Web Developer, Game Developer, and Software Programmer.
The Need for Cybersecurity
In the post-pandemic era, the world economies are now interconnected by supply chains, technology, and travel. The rapid climb of the number of appliances, devices, vehicles, and infrastructure are linked which is foremost to the overly interconnected world. LNCT is the best BTech Cybersecurity College in Bhopal.
The rise in demand for digitization services creates a network of Internet of Things devices to enable a better consumer experience but also raises the high incidence of cyber attacks.
Cybersecurity jobs now are one among the foremost compelling jobs for college kids. The demand for jobs in Cybersecurity growth is unmatched in the other technology domains. Companies across the world are continuously targeted for cyber-Attacks. LNCT is the best BTech Cybersecurity College in Bhopal.
This scenario has given massive opportunities for professionals willing to enter the safety domain. Cybersecurity today is a serious source of employment and a lucrative career option. The initiative is to accumulate basic Cybersecurity skills, followed by choosing a selected domain that supported personal interest, preferences, and market demand. LNCT is the best BTech Cybersecurity College in Bhopal. In order to have a promising future prospectus, aspirants should get deep knowledge and training, enhance their skills, and obtain security certifications. LNCT is the best BTech Cybersecurity College in Bhopal.
While other sorts of IT jobs like software developers or network administrators are more familiar and well-known, Cybersecurity jobs are smaller in number but are fast increasing in importance. LNCT is the best BTech Cybersecurity College in Bhopal.
As our worldwide economy has led to more Internet-based computing and connectivity the world over, organizations have grown ever more susceptible to hacking and cyber-attacks. Even when there are area police, so must a business hire cyber staff. LNCT is the best BTech Cybersecurity College in Bhopal.
It’s ultimately the duty of the organization to guard their data also as any customer information they’re liable for. Over the course of years, the worldwide importance of Cybersecurity has continued to grow. LNCT is the best BTech Cybersecurity College in Bhopal.
Organizations have now beginning to understand that malware is the publicly available commodity that creates it easy for anyone to become a cyber attacker or intruder, and even more, companies provide solutions in security that do little to defend against attacks. Cybersecurity demands focus and dedication. LNCT is the best BTech Cybersecurity College in Bhopal.
Cybersecurity aims to guard the information and integrity of computing assets belonging to an organization’s network. Its purpose is to defend and protect those assets against all threat actors throughout the whole life cycle of a cyber attack. LNCT is the best BTech Cybersecurity College in Bhopal.
Cybersecurity’s importance is on the increase in contemporary times. Principally, our society is more technologically reliant than ever before and there’s no sign that this trend will hamper any time soon. LNCT is the best BTech Cybersecurity College in Bhopal.
Data leaks that would end in fraud are now publicly posted, sensitive information like Social Security numbers, MasterCard information, and checking account details are now stored in cloud storage services like Dropbox or Google Drive. The very fact of the matter is whether or not we are a private, small business, or large multinational; we rely on computer systems every day. LNCT is the best BTech Cybersecurity College in Bhopal.
On keeping this with the increasing rise in cloud services, poor cloud security services, smart-phones, and therefore the Internet of Things (IoT).
We have an innumerable number of Cybersecurity threats that did not exist a couple of years ago. We’d like to know the importance of Cybersecurity. Governments around the world are now paying more attention to cybercrimes and related aspects. LNCT is the best BTech Cybersecurity College in Bhopal.
-
Cyber Crime
Information theft and fraud are among the foremost expensive and fastest growing segments of cybercrime, largely driven by, the increasing exposure of identity information to the web by the means of cloud services. LNCT is the best BTech Cybersecurity College in Bhopal.
But it’s not the one and only target, Industrial controls that manage power grids and other infrastructure are often disrupted or destroyed. And fraud is not the only goal, cyber attacks may aim to compromise the integrity of data- destroy or change data, to breed distrust in a corporation or government. LNCT is the best BTech Cybersecurity College in Bhopal.
Cybercriminals are getting more versatile and complicated, changing what they aim, how they affect organizations, and their methods of attack for various security systems. Social engineering remains the simplest sort of cyber attack, with, phishing, ransomware, and spyware being the simplest sort of entry.
Third-party and fourth-party vendors who process the info and have poor Cybersecurity practices are common attack vendors, making vendor risk management and third party risk management all the more important. LNCT is the best BTech Cybersecurity College in Bhopal.
Data breaches can involve financial information like MasterCard numbers or checking account details, protected health information, personally identifiable information, trade secrets, property, and other such possible targets. Other terms for data breaches include unintentional disclosure of data, cloud leak, data leak, information leakage, or a knowledge spill. LNCT is the best BTech Cybersecurity College in Bhopal.
Alongside these, other factors that drive the expansion of cybercrime are the distributed nature of the web. The criminals have the power to attack targets outside their jurisdiction, which makes policing them extremely difficult. LNCT is the best BTech Cybersecurity College in Bhopal.
The increasing usage of the dark web, for for-profit and commerce purposes too, contributes to the same. The proliferation of mobile devices and the Internet of Things, has increased the danger of cybercrime and therefore the need for Cybersecurity. LNCT is the best BTech Cybersecurity College in Bhopal.
These Cybersecurity professionals are brief in supply, however. Last year, a report from NASSCOM stated that India alone would need 1 million Cybersecurity professionals by 2021, while the job portal indeed reported hiking an all time high of 150 percent in Cybersecurity roles between January 2017 and March 2018. LNCT is the best BTech Cybersecurity College in Bhopal. Companies like KPMG have doubled the dimensions of their Cybersecurity teams in recent years. The present overwhelming need for Cybersecurity is that the result of many factors a number of which include:
-
Digital India and Demonetization
According to a senior director of NASSCOM, Ashok Pamidi, while the government’s initiatives like Digital India and demonetization have pushed companies towards the much needed digital transformation, doing so has also made them increasingly vulnerable and in danger to cyber-attacks.
In turn, this has led to a requirement for Cybersecurity professionals who can help companies achieve digital transformation without compromising security. LNCT is the best BTech Cybersecurity College in Bhopal.
-
Consequences of WannaCry Ransomware
In May 2017, government agencies and organizations across the world fell prey to the WannaCry ransomware, which infected over 200,000 computers in 150 countries within three days. Consistent with the newest numbers, it led to wreck estimated up to many billions of dollars. LNCT is the best BTech Cybersecurity College in Bhopal.
The attack launched a heated and long drawn debate on the vulnerability of knowledge and therefore pressing the need for stronger cyber laws and security systems. It also caused many organizations to be more conscious of the perils of Cybersecurity loopholes and take steps to safeguard their organization from such attacks in the future. What is Cybersecurity is a question that often comes in mind.
-
General Data Protection Regulation (GDPR)
Companies across the world are preparing to safeguard their database from cyber crimes and suits the principles of GDPR. This has driven a requirement for Cybersecurity experts. A scarcity of specialized individuals in Cybersecurity can damage businesses in a range of ways including:
- Regulatory costs: data breach laws mean that your organization or firm could suffer from regulatory fines or sanctions as a result of cybercrimes.
• Economic costs: Theft of property, corporate information, disruption in trading, and therefore the cost of repairing damaged systems and end in huge economic loss.
• Reputational costs: Loss of the trust of consumers along with loss of current as well as future customers to other competitors and media coverage that is poor.
Looking at the character of cybercrime and the way how difficult it’s to detect it, it’s difficult to know the direct and indirect costs of the many security breaches. Although this does not mean the reputational damage of even a little data breach or other security hazards isn’t large. If anything, consumers expect increasingly sophisticated Cybersecurity measures as time goes on and passes. LNCT is the best BTech Cybersecurity College in Bhopal.
All businesses, no matter the dimensions, small and enormous must ensure all staff understands the importance of Cybersecurity threats and the way to mitigate them. This could include regular training for an equivalent and a framework to figure with thereto aims to scale back the danger of knowledge leaks and breaches. LNCT is the best BTech Cybersecurity College in Bhopal.
Case Study Highlighting the Importance of Cybersecurity: What is Cyber Security
Courtesy: eBay
eBay, the world’s largest and most used eCommerce platform, suffered a serious security breach in 2014. Quite a 100 million users had been affected in what has become one of the most important cybercrime thus far. It’s still not clear how the intruders gained access to the eBay databases, but this is often definitely got the authorities to take Cybersecurity seriously. LNCT is the best BTech Cybersecurity College in Bhopal.
Identity and data theft has become a significant issue in recent years. The aforementioned eBay breach remains to create waves as many usernames, passwords, phone numbers, and physical addresses are stolen. LNCT is the best BTech Cybersecurity College in Bhopal.
“Cyber-attackers compromised a number of employee log-in credentials, allowing unauthorized access to eBay’s corporate network, The company is aggressively investigating the matter,” eBay commented.
What’s really happened in eBay?
The hacking, which was examined by security experts, reported that the access was created after hacking into an eBay employee’s computer. The technique used to execute the cybercrime has not yet been revealed, but the criminals have also managed to steal hashed passwords that aren’t exactly “uncrackable”.
eBay is additionally vulnerable to XSS attacks and other hacking methods. Security expert Jordan Jones showed how eBay’s Research Labs page is often infiltrated with the assistance of an easy code of XML. In another research, Michael E found how to open bogus auction pages with illegal JavaScript scripting and harvest user cookies without their knowledge.
“It’s not surprising that eBay’s site was breached. Attacks like this will definitely be considered the new norm,” Checkmarx founder and CTO Maty Siman explained, “Organizations got to take more security measures to guard their digital assets against the outset by examining their ASCII text file for vulnerabilities and eliminating them beforehand .”
Millions of eBay users were asked to vary and update their passwords.
The eBay breach is one of the variables that have stirred the officials into action to require Cybersecurity seriously.
Organizations cannot afford to lose all the info to the hackers, who then use it to take advantage of the privacy of the individuals.
eBay isn’t the sole company that suffered breaches in privacy, a number of documented examples are-
- Equifax: The Equifax cybercrime fraud, affected approximately 145.5 million U.S. consumers along side 400,000-44 million British residents and 19,000 Canadian residents. Equifax shares dropped 13% in early trading the day after the breach; numerous lawsuits were filed against Equifax as a result of the breach not to mention the reputational damage that Equifax suffered. On July 22, 2019, Equifax agreed to a settlement with the FTC including a $300 million fund for victim compensation, $175m for states and territories within the agreement, and $100 million in fines.
- Yahoo: Yahoo disclosed that a breach in August 2013 by a gaggle of hackers had compromised 1 billion accounts. During this instance, security questions and answers were also compromised, increasing the danger of fraud. The breach was first reported by Yahoo on December 14, 2016, and made all affected users vary passwords, and re-enter any unencrypted security questions and answers to form them encrypted within the future. However, by 2017 October, they changed their estimate to three billion user accounts. An investigation revealed that users’ passwords in clear text, payment card data, and bank information weren’t stolen. Nonetheless, this remains one of the most important data breaches of this sort in history.
- Adult Friend Finder: In October 2016, hackers collected 20 years of knowledge on six databases that included names, email addresses, and passwords for The Friend Finder Network.
The FriendFinder Network includes some websites such as Penthouse.com, Adult Friend Finder, Cams.com, Stripshow.com, and iCams.com. Most of the passwords were protected only by the weak SHA-1 hashing algorithm, which meant that 99% of them had been cracked by the time LeakedSource.com published its analysis of the whole data assails on November 14.
Such instances have made it amply clear that our networks and our personal information can easily be accessed if we don’t possess some full proof security software, which will protect our data base from the attacks of such hackers and malware. There had been problems like these at both the private and professional levels that have created the demand for Cybersecurity experts.
These are the people that are tasked with studying digital networks to seek out the weak points which may provide quick access to hackers and malware, and designing stronger systems that might leave the safe transfer of encrypted data over those networks. As hackers grow bolder, sophisticated, and better equipped, the demand for Cybersecurity experts will only rise in the future. Security against malware is certainly one of the foremost important issues today and it’ll still be as malicious software evolves.
An anti-virus software package is required to combat any suspicious activity. These packages include tools that do a lot of things from warning against websites that are suspicious to flagging potential emails that may be harmful.
We must be extremely careful while browsing such websites and other online platforms. To guard their customers, from the invasion of privacy, the organizations too should install anti-viruses and recruit Cybersecurity professionals, who will help them from hackers and malware. It’s only by this, could they hope to offer a secure environment to their users.
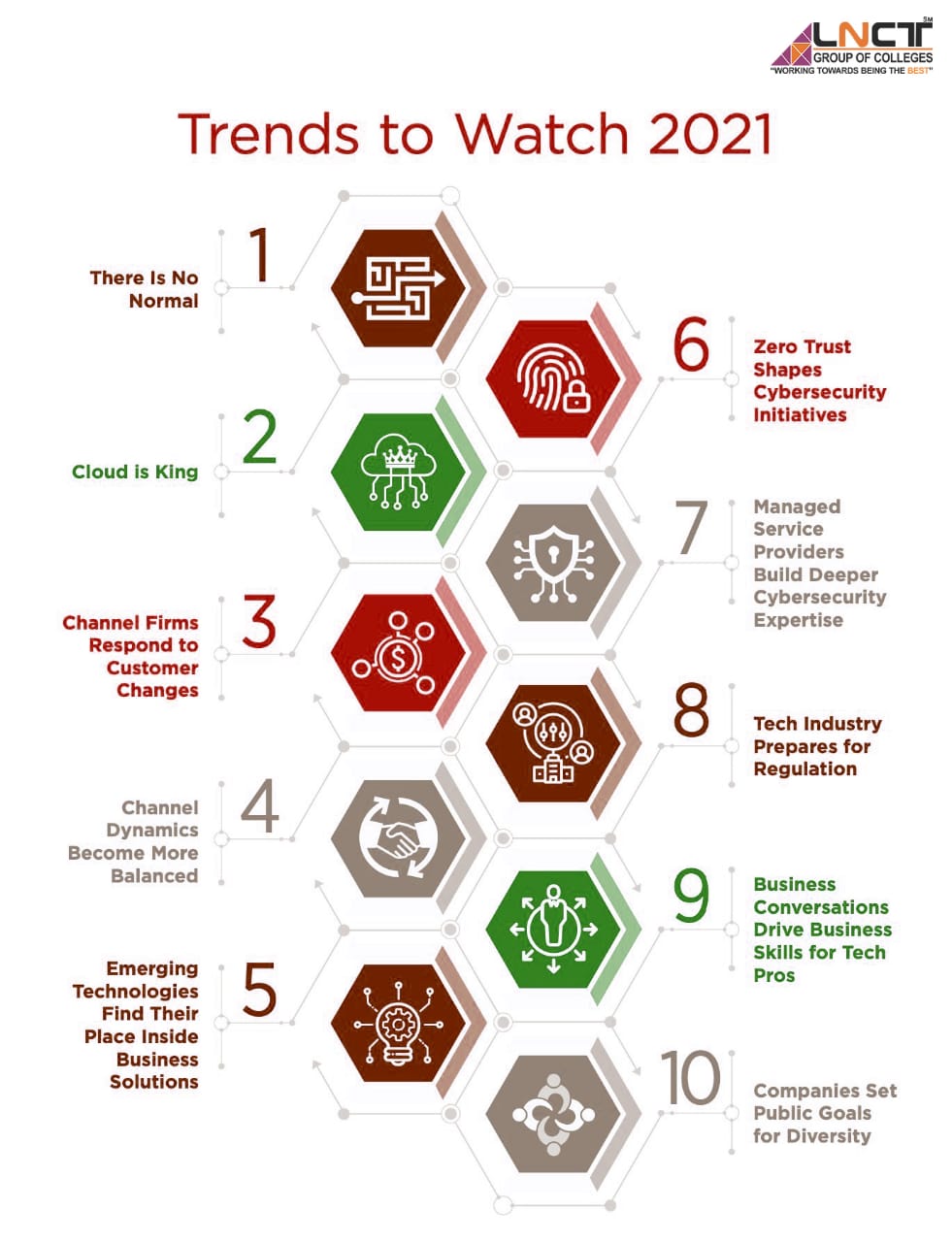
Trends in Computer sciences and Cybersecurity
As the world advances to increasingly Digital and Tech-savvy times, space is about to note an important amount of changes in their prevailing trends. The normal methods won’t stand and hold valid and must be changed or improvised to stay up with the trends. LNCT is the best BTech Cybersecurity College in Bhopal.
With the expansion of completely new technologies especially cloud computing and machine learning, it’s fair to expect that the speed of change will increase in 2021 and within the coming years. Blockchain technology and standardization of knowledge are two instances of the same. The chapter attempts to trace these changing trends, which will impact the individuals related to the sector of science and technology. LNCT is the best BTech Cybersecurity College in Bhopal.
Blockchain is a list of records called blocks that store data publicly in a systematic and chronological order. The knowledge is encrypted using cryptography and other such techniques to make sure that the privacy of the user isn’t compromised and data can’t be altered. LNCT is the best BTech Cybersecurity College in Bhopal.
Information on a Blockchain network isn’t controlled by any of the centralized authorities, very unlike modern financial institutions. The participants of the network maintain the info, and that they hold the authority to approve any transaction which may happen on the network. LNCT is the best BTech Cybersecurity College in Bhopal.
Therefore, a typical Blockchain network may be a property right. As long as someone has access to the network, you’ve got access to the info within the Blockchain. If you’re a participant within the Blockchain network, you’ll have an equivalent copy of the ledger, which all other participants have. Albeit one node or data on one particular participant’s computer gets corrupted, the opposite participants are going to be alerted immediately, and that they can rectify it as soon as possible.
Quantum Computing
It is the utilization of quantum physics, like superposition and entanglement, to perform computations. It uses quantum bits in a similar way that regular computers use bits. Quantum computers have the potential to unravel problems that might take the world’s most powerful supercomputers many years.
Companies including Google, Microsoft, and IBM are all competing to create reliable quantum computers. In fact, In September 2019, Google AI and NASA jointly published a paper that claimed to possess achieved “quantum supremacy”. Quantum computers could completely revolutionize and transform data sciences.
They even have the potential to accelerate the event of AI, computer games, big data, deep learning, encryption, medicine, and more. The downside is that quantum computers are currently incredibly difficult to create and sensitive to interference.
Despite current limitations, it’s fair to expect further advances from Google, etc. which will help make quantum computers practical to use, which might position quantum computing together as the foremost important computing trends of the approaching years.
Zero Trust
Most information security frameworks employed by organizations use traditional trusts authentication methods like secure codes and passwords, these frameworks specialize in protecting network access, and that they assume that anyone that has access to the network should be ready to access any data and resources they’d like. There is a big demerit to the present approach.
Zero trust information security models aim to stop this. They replace the old assumption that each user within an organization’s network is often trusted. Ideally, trust is no given to anyone, even if they are already inside the network. Verification is required from everyone trying to realize access to any resource on the network.
This security architecture is quickly moving from just a computing concept to industry best practice. It’s been found that the typical data breach costs a corporation some $3.86 million of injury, and thus, it’s important to recruit IT professions and Cybersecurity professionals to stop such havoc. We’ll see a requirement for this technology skyrocket in 2021 as businesses adopt Zero Trust security to mitigate this risk.
Cloud Computing
Gartner has estimated that 80% of enterprises will pack up their old traditional data centers by 2025. This is often mainly because traditional cloud computing relies on servers in only one central location. If the end-user is in another country, they need to attend while data travels thousands of miles.
Latency issues like this will extremely hamper an application’s performance. Therefore, companies are moving over to edge computing service providers instead. Modern age computing conducts computation, analysis of data, and data storage, as close as possible to the end-user location. And when edge servers host web applications the result’s a massively improved reaction time.
Demand of Cybersecurity
As a consequence, large numbers of companies seek Cybersecurity expertise to guard themselves and their customers. HackTheBox is one such online platform that features a wealth of educational information and many Cybersecurity-themed challenges. LNCT is the best BTech Cybersecurity College in Bhopal.
They have a great number of active users that test and improve their skills in penetration testing. So, they’ve become the go-to place for companies to recruit new talent for his or her cybersecurity teams. LNCT is the best BTech Cybersecurity College in Bhopal.
Specialized Courses, Job Prospectus and the Scope of Employment; What is Cybersecurity contributing to different sectors
Industries like health care, finance, manufacturing, and retail all hire Cybersecurity professionals to guard valuable information against cyber breaches and intrusion. The demand for specialists within the field is extremely high. LNCT is the best BTech Cybersecurity College in Bhopal.
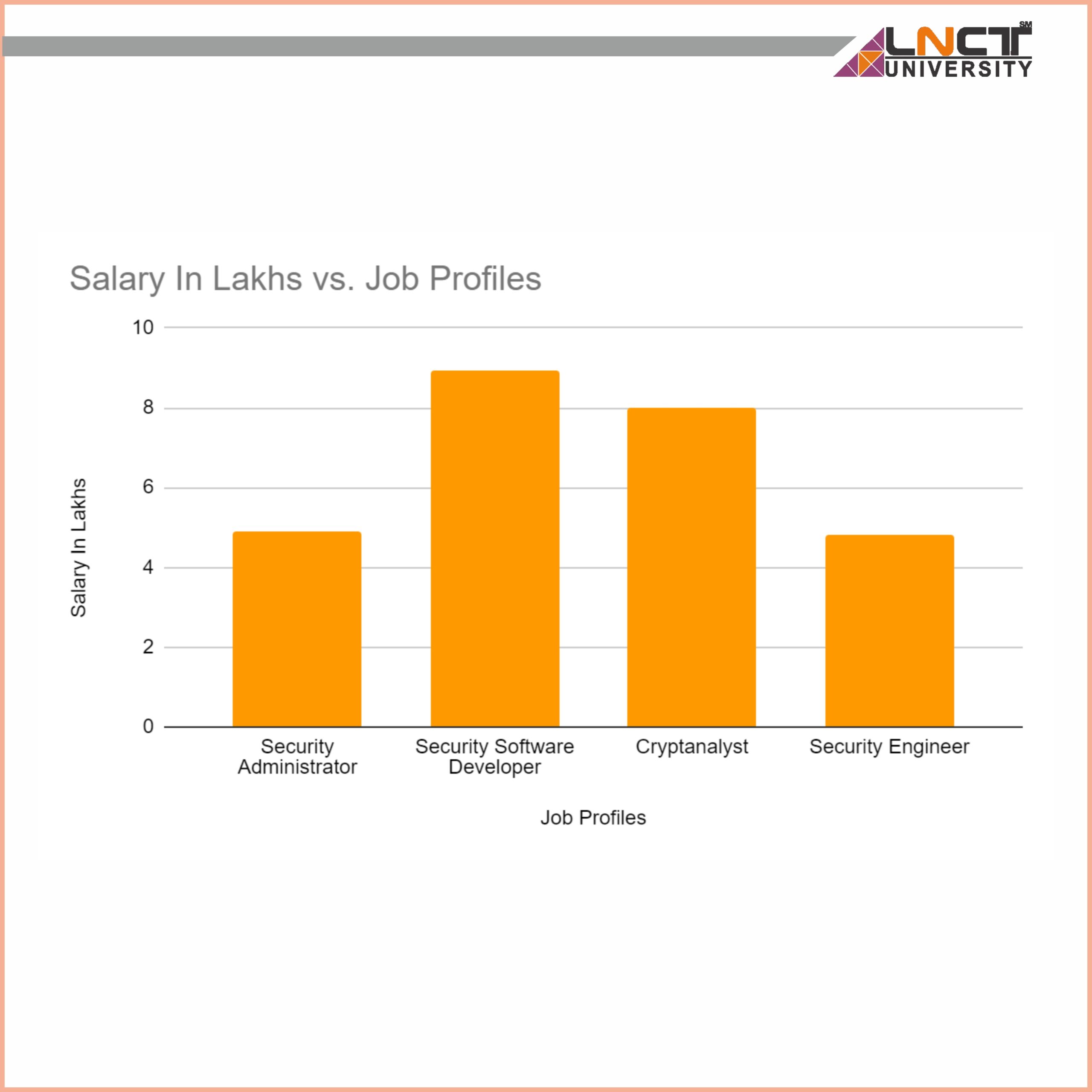
A report by job analytics firm Burning Glass Technologies found job postings for openings in Cybersecurity have grown 3 times faster than those for IT jobs overall, and Cybersecurity professionals are earning up to 9 percent quite their IT counterpart
Chief Information Security Officer
The chief security officer is directly liable for coordinating, planning, and directing all computer, network, and data security needs. CISOs. Is typically a mid-executive level position, whose job is to oversee the overall operations of a corporation’s IT security division.
They directly work with upper level management to style the organization’s security needs. They’re commonly tasked with assembling an efficient staff of security professionals, therefore, a robust IT background and strategy management may be a prerequisite skill along side personnel management is required for the same.
Information Security Analyst
An information security analyst is liable for the protection of an organization’s computer systems networks. They plan and execute programs and other measures, including installing and using software of knowledge encryption and firewalls.
Additionally, security analysts help design and execute plans and methods for the recovery of knowledge and system following a cyber attack. ISAs must continuously stay at the highest of the ladder and must know the newest industry trends and cyber threats, which involves researching new security technologies and networking with other professionals.
Penetration Tester
These professionals are concerned with the increased and proactive authorization for workers for testing techniques thereon infrastructure to spot system vulnerability. Penetration testers attempt with full authorization to hack into the computer and network systems to pre-emotively discover OS vulnerabilities, services and application problems, improper configurations, and more before outside intruders have the chance to cause any quite real damage.
Penetration testers must be highly creative and innovative in their methods, often using testing tools of their own design, to interrupt the system under scrutiny. Penetration testers are required to stay careful records of their activities and discovered vulnerabilities, which can eventually help them to correct their mistakes in the future.
IT Security Engineer
Security engineering provides a specialized approach to Cybersecurity, specifically regarding the planning of security systems to counter potentially catastrophic issues.
They’re often involved in system maintenance, performing security checks to spot potential vulnerabilities, also on keep logs, and developing automation scripts to trace various security incidents. To succeed as an IT Security Engineer, individuals must have strong math and communication skills and a solid working knowledge of operating systems and languages.
Security Architect
A Security Architect is liable for establishing and maintaining network security for the organization. Security architects add all types of sectors for the economy of companies, government agencies, etc.
Security architects develop and implement organizations’ security policies and procedures for workers, with access to computers, networks, and data systems. Security architects are liable for the hands-on immediate repairing of issues raised in problem reports and therefore the analysis of breaches following the safety incidents.
IT adviser
These consultants meet with potential clients to advise them on the way to best protect their organization’s Cybersecurity objectives efficiently. They’re hired by both small scale and large scale organizations, to supplement their security needs and supply them with an unbiased perspective of their current system. They supply predictive models to correct an equivalent. Working as an IT adviser demands long and versatile hours and involves a fair amount of travelling so as to satisfy clients.
Security System Administrators
A Security System Administrator’s responsibilities include installing, administering, maintaining, and troubleshooting computer, network, and data security systems.
They’re normally the person responsible for the daily operations of these security systems, their typical task includes system monitoring and running regular backups, and fixing, deleting, and maintaining user accounts. They’re often involved in developing organizational security procedures.
Forensic Computer Analysts
Forensic Analysts are the cyber world detectives. These analysts assess that information based o computer for confirmation following a security breach or other incident. Their tasks include handling hard drives and other storage devices and employing specialized software programs to spot vulnerabilities and recover data from damaged or destroyed devices.
They need to be sensitive to the safety concerns of the organizations and employers and closely follow all privacy procedures with financial and private information. They need to also keep detailed and accurate logs and records of their findings, which are often utilized in litigation.
Courses Offered
Students can pursue B. Tech or B. Sc Degree in Cybersecurity and computing after the completion of their higher education. B. Tech degree programs in Computer Sciences and Cybersecurity are conducted for a duration of four years, and B. Sc in Cybersecurity/ Computer Sciences may be a three-year-long course duration. Aside from these are various courses that are offered in various fields under this umbrella genre, a number of which include a Diploma in Ethical hacking and Programming languages. LNCT is the best BTech Cybersecurity College in Bhopal.
Following is an approximation of the courses offered for specializing in Computer Sciences and Cybersecurity.
- B.Tech or M.Tech Computer Engineering with Cybersecurity
• B.Tech or M.Tech Computer Engineering with Cybersecurity and Networking
• B.Tech or M.Tech Computer Engineering with Forensics and Cybersecurity
• B.Tech or M.Tech Computer Engineering with Certified Cybersecurity Investigator
• B.Tech or M.Tech Computer Engineering with Quick Heal and Cybersecurity
• B.Sc Cybersecurity
• B.E Information Technology with IBM
• B.Sc Information Cybersecurity and Technology Management
• BCA Hons. In Cybersecurity
The mentioned courses, inculcate essential skills that enable individuals with pre requisites to figure within the computer and tech sector. With the changing times, it has apparently become clear that the demand for specialists will grow and corporations will heavily recruit individuals to guard themselves and therefore protect themselves from hackers and intruders. LNCT is the best BTech Cybersecurity College in Bhopal.
Employment
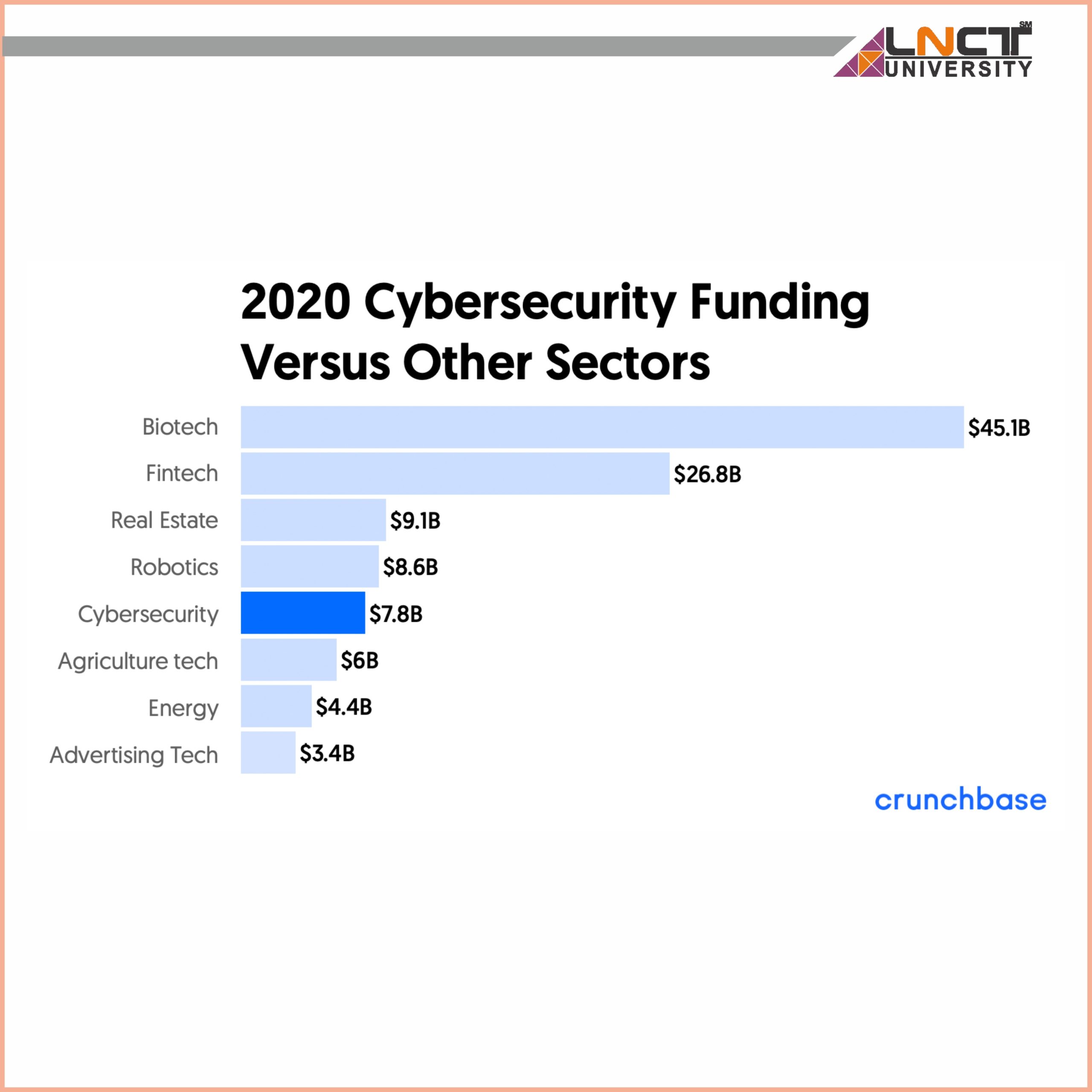
We are currently facing a worldwide Cybersecurity shortage, consistent with a recent finding, from Indeed. Job postings within the Cybersecurity field have gone up to 74% over the past five years, while a Cisco report estimates that there are currently 1 million unfilled Cybersecurity jobs worldwide.
Symantec has predicted that this shortage will only grow, which we’ll see 1.5 million unfilled jobs within the field by 2019.
“Part of the rationale these roles are so hard to fill is because there simply aren’t enough job seekers looking to figure in these positions, indeed research has shown that the foremost in-demand Cybersecurity titles consistently don’t receive interest from job seekers that’s like the amount of job postings within the field.”
– Daniel Culbertson, Indeed economist
As organizations across a good range of various industries like banks, government, retail, and BFSI sectors actively recruit Cybersecurity professionals, the work demand will only go up.
The challenge is to satisfy that demand by ensuring people are becoming trained for these critical security roles. And once they’re trained, exciting and well-paying jobs are going to be available for them, which will end in a promising future.
Apple
At the highest of the list, Apple has seen several important battles around the privacy and security implications of encryption and IOS–most recently, attorneys have requested the corporate to return to operating systems that make it easier for enforcement officials to extract data.
It’s possible that the corporate is hiring more cyber professionals to continue bolstering that employment in these areas and protecting user data. Apple is the world’s most technologically advanced company that recruits an outsized number of IT professions, software developers, and other such individuals.
Lockheed Martin
The Global Security and aerospace company Lockheed Martin employs approximately 97,000 people worldwide. Since it’s involved within the research, development, manufacturing, and integration of advanced technology systems and products, the corporate is probably going to add more positions in cybersecurity to guard those offerings.
General Motors
Auto giant General Motors has made several moves into the connected cars and autonomous cars space within the past few years. It invested $500 million into Lyft, partially to figure on the company’s plans for a driverless car fleet; this surely requires an outsized amount of IT individuals to accomplish such a fleet. These automated cars possess security risks that may be tackled by professionals and the development teams.
Cisco
Cisco has reported that cyber attacks are becoming stronger and features a number of cybersecurity efforts and products in situ. As they continue, researching and tackling the problems, they readily employ IT professionals to strengthen their space.
Intel
As Intel moves further into the web of Things (IoT) space with new chips and other devices, they’re heavily recruiting staff to stay those devices from being hacked.
Northop Grumman
Northrop Grumman is a security company that works on a global level aiming to provide systems and products to government and commercial customers. The corporate invests in research on identity management, cloud security, and provide chain, and more, and is probably going to feature more staff to make sure high-profile systems are kept secure.
Boeing
Airplane manufacturer Boeing is experimenting with using next-generation technology. They recently partnered with Microsoft to use the company’s AI and large data analytics tools to enhance operational efficiency. Boeing is additionally working with other firms and using the Skylight platform to interface with its manufacturing system and work instructions with wearable devices. Therefore, the corporate will need upgraded security capabilities to stay these tools functioning.
Microsoft
Microsoft is that the biggest software company that makes software and enables the working of electronic devices- like computers, smartphone,s etc. an outsized number of the population is very trusted with Microsoft for their tech needs. Microsoft recruits an outsized number of Computer engineers, software developers, cybersecurity specialists, and more. What is Cybersecurity is a question that often comes in mind.
Besides the aforementioned companies, an excellent number of firms and personal industries that deal is web development services and marketing too readily employ computing graduates and Cybersecurity specialists to enhance their scope of surviving within the coming times. It’s the facility of those informed individuals which will save the world of computers and Cybersecurity from many dollars worth of injury.
Conclusion; What is Cybersecurity & How it will change our world
In these changing times where the world is becoming increasingly contingent in science and technology, the danger of cyber crime is increasing and thus the protection of knowledge and private details may be a major aspect of the organizations and firms, therefore there’s a high demand for computer scientists and Cybersecurity professionals. LNCT is the best BTech Cybersecurity College in Bhopal.
Tech firms, like Google and Microsoft readily employ professionals for the same, because the hackers and intruders are getting increasingly efficient and effective in intruding into the private space of firms and corporations and violating data, this has increased the importance of Cybersecurity specialists. LNCT is the best BTech Cybersecurity College in Bhopal.
As the world is increasingly growing tech-savvy, and therefore the field of AI, Robotics, Data Analysis is spreading wings, so is the risk of breach of privacy, and therefore, a good range of jobs is projected to grow in various fields, starting from software to consultancy to marketing, professionals are employed as analysts, security consultants and more. LNCT is the best BTech Cybersecurity College in Bhopal.
The statistics, promise a bright future within the respective field and it can be fairly concluded that aspirants must be encouraged to pursue them. The sector of science and technology promises a bright and fulfilling future with a multitude of job opportunities. LNCT is the best BTech Cybersecurity College in Bhopal.
It’s only these professionals and specialists who will help the world grow digitally and make human lives easy, but on the opposite hand, it’s equally important to guard data by creating strong security systems and firewalls so as to not let intruders violate them. It’s important to take care of a transparent trusting relationship between the firm and its customers which may be only achieved with professionals who are highly trained in Computer Sciences and Cybersecurity. LNCT is the best BTech Cybersecurity College in Bhopal.
Check out:
Placement Record of LNCT Bhopal 2020-21 batch
Dream job offers to the 2021 batch students of LNCT Bhopal
Also read:
Best Science College in Bhopal